What are VPN
According to wikipedia:
A virtual private network (VPN) extends a private network across a public network, and enables users to send and receive data across shared or public networks as if their computing devices were directly connected to the private network. Applications running across a VPN may therefore benefit from the functionality, security, and management of the private network.
VPN technology was developed to allow remote users and branch offices to securely access corporate applications and other resources. To ensure security, data would travel through secure tunnels and VPN users would use authentication methods - including passwords, tokens and other unique identification methods - to gain access to the VPN. In addition, Internet users may secure their transactions with a VPN, to circumvent geo-restrictions and censorship, or to connect to proxy servers to protect personal identity and location to stay anonymous on the Internet. However, some Internet sites block access to known VPN technology to prevent the circumvention of their geo-restrictions, and many VPN providers have been developing strategies to get around these roadblocks.
VPNs cannot make online connections completely anonymous, but they can usually increase privacy and security. To prevent disclosure of private information, VPNs typically allow only authenticated remote access using tunneling protocols and encryption techniques.
The VPN security model provides:
- confidentiality such that even if the network traffic is sniffed at the packet level (see network sniffer and deep packet inspection), an attacker would see only encrypted data
- sender authentication to prevent unauthorized users from accessing the VPN
- message integrity to detect any instances of tampering with transmitted messages.
Well our focus in this article is not on VPN but something that is new in market called Double VPN.
Double VPN and its security
Double vpn service simply use two vpn server through which all your traffic pass. It adds an extra layer of vpn security which an attacker need to handle. If user A want to send message to some site B then the whole message travel through Vpn A and Vpn B.
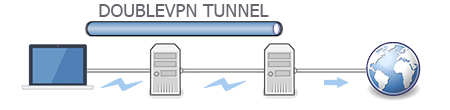
If an attacker doing MITM somewhere between A and VPN A then all he got is encrypted message inside an vpn tunnel which is very difficult to decrypt. Although he can get the source address but still destination address is unknown to him. Same think will happen if attacker is between VPN A and VPN B but the thing that only changes is that he doesn’t even have source address. To get the source address he need to first get a control over VPN A server’s traffic.
In case if the attacker is between VPN B and B then he gets the unencrypted and non tunneled data but he doesn’t have source address and he will need to dealt with both VPN A and VPN B server to get source address, which is one extra step as compare to using a single vpn.
Double vpn looks quite secure but it also have some issues which overshadows its usability like slow surfing speed due to tunneling through two different servers A→VPN A → VPN B → B. You may also need to pay to two different vpn providers until its not default provided by your Vpn provider like NordVpn.
Possible attack on vpn data encryption
Declaimer:Below information is hypothetical and may not work in practical.
If you are using VPN then all your data travel to your system to vpn server is encrypted. Usually encryption used by vpn provider are either DES or AES 256-bit. Lets take an example case where a vpn provider is using DES encryption for data.
If you are using two different vpns then your data get encrypted twice with two different keys K1 and K2. If a attacker is spying between both A to VPN A and VPN A to VPN B. In that case finding the key K1 and K2 will be his priority. For single encryption the key space is 2^56 and its seems for double encryption the key size should double but that is not the case here due to Meet in the middle attack in double decryption.
The attacker knows plaintext p(between A and VPN A) and ciphertext c(between VPN A and VPN B).
Here is double encrytion:
p→ E(K1, p)→ E(K2, E(K1, p)) =c
If he try all 2^56 the keys to encrypt p and store their result and also try to decrypt c using all 2^56 key pair. After each decryption he will check for a match with stored output of encrypted p. When he have a match he get the located key pair used in both vpn encrytion. So, it only take him twice as long as to break double DES. This makes security here 2*2^56=2^57 which is very less then expected 2^112.
Is double vpn worth?
Double vpn is a good solution with compromised in speed and extra money, it provides an extra layer of security but it is not a must have solution as there is better alternative available that can be more powerful. Tor uses the same concept of transferring data through multiple relay nodes (can be treated as VPN servers) and uses diffie hellman for key exchange. Also if the vpn servers are not trusted and is been affected by Five eyes agencies then there is not much point of using the vpn for your anonamity. Instead he/she can opt for using tor network which uses relay nodes randomly from tor users. So, someone not happy with single vpn service can use tor network which is free and open source instead of going for double vpn.
What about tor and how safe is it?
The name tor is derived from an acronym for the original software project name "The Onion Router". Tor directs Internet traffic through a free, worldwide, volunteer overlay network consisting of more than seven thousand relays to conceal a user's location and usage from anyone conducting network surveillance or traffic analysis.
If you are using internet with a registered identity then it is tough to say that you can ever been absolute anonymous. But what you can archive is pseudo anonymity which provides you good enough anonymity in place of perfect anonymity. Tor is by far the best practical solution available for pseudo anonymity.
With high security budget and high amount of resources used by spy agencies it is really tough to say that any forms of digital security cannot be breached. But whole point of using tor service is to make it so much of a challenge to do, that the resources are better spent elsewhere. Tor is a big success in archiving that. Altough tor also have its own caveat and flaws but most of the time in past, deanonymizing of a user or a group of users has made possible by using security flaws present not in tor but on some other services or due to user’s own mistake. Lets take a look into few limitations that tor network consist or mistakes that a user can do which are mostly result for deanonomizing people from tor network.
DNS leaking
When using tor network, it is extremely important that all traffic originating from your computer is routed through the tor network. If any traffic leaks outside of the secure connection to the network, any adversary monitoring your traffic will be able to log your activity.
Most Internet service providers assign their customers a DNS server which they control and use for logging and recording your Internet activities. DNS or the domain name system is used to translate domain names into IP addresses which are required to route packets of data on the Internet.
If all your traffic is not routing trough tor network it may possible that your operating system revert back to use the default dns server provided by ISP. Because of that all the site you are visiting will get logged by your isp.
Issues related to browser
If you are using tor bundle it is important to use only default tor browser and always use tor network for better privacy. Tor browser is configured to work best for tor network and doesn’t leaks any information. If you are using a system default browser like chrome maybe any previous saved cookie on some site having details like your login name or any other juicy information may demystify your identity to the site server.
Man in the middle issue
Data in tor network goes encrypted from user to guard node and in between relay nodes till exit node.
But after exit node the data goes in unencrypted manner. So, if an attacker somehow now your exit node or is already doing MITM between exit node and destination can see the data in unencrypted form.
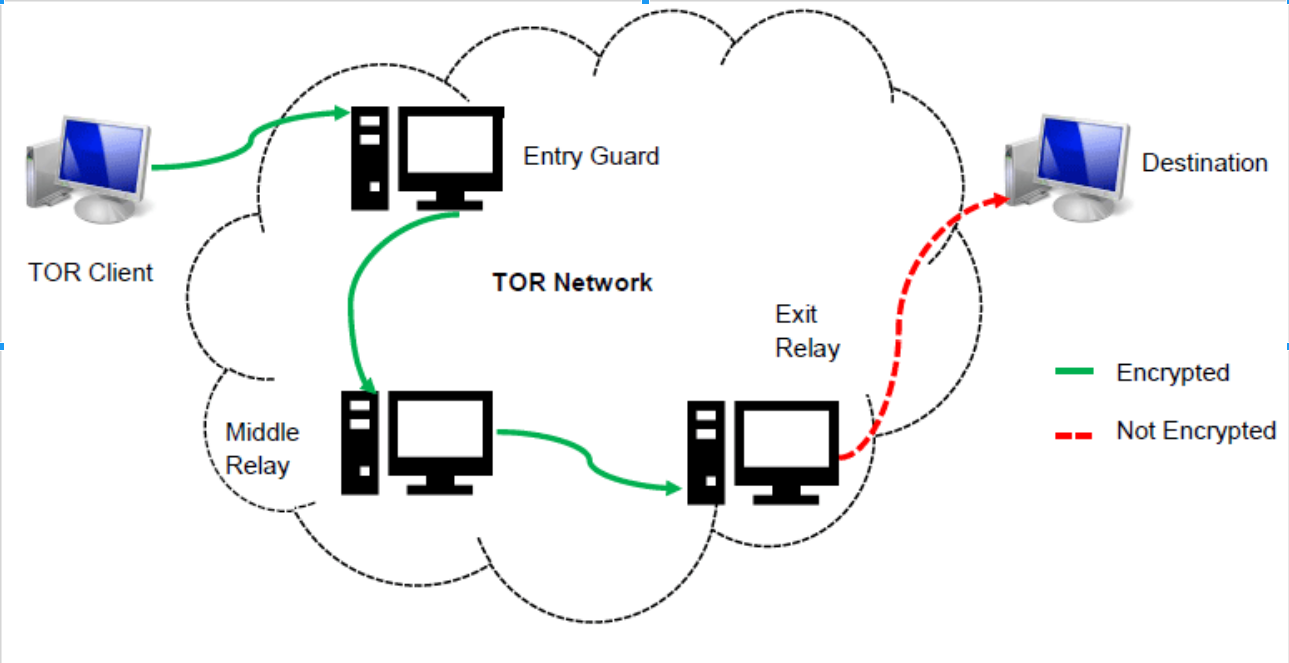
But it is worth to remember that there is almost very less way through which an attacker doing mitm between exit node to destination will able to find out the source where the traffic is coming from since each node are only aware of their neighbor nodes only.
Correlation attacks
It has been reported by lots of security experts and through government leaks that NSA is spending quite a high amount of money and resources to deanonymizing people over tor network. It has been said that huge amount of tor guard nodes and exit nodes are run by government itself to log the users activities over tor network. If a user’s both of these node by chance where monitored by some agencies then by network traffic pattern the incoming traffic to guard node and outgoing traffic from exit node can be correlated on the basis of timing and data properties to find traffic of a particular user. For example if you send a 5 MiB file over a tor network, it suppose to have size of 5.5 MiB from source to
guard node(extra size due to encryption) and 5 MiB from tor exit to destination. So, an attacker can easily found out that by data size that its a particular user’s traffic going through.
Although to stop these type of attacks few adaptations changes have been done by tor developers earlier like giving option to select guard and exit node based on different locations and fragmentation of packets but totally patching these type of attacks are quite difficult because the attack is not happening due to flaw in software but is just a logical analysis.
There are few more ways through which users lose their anonymity but none of them is actually flaw in Tor itself but either a limitation which cannot or difficult to be improve or a user’s own mistake like login and using your gmail while surfing through tor network. So, key point to remember is that for a better anonymity you not only need tor for privacy but you also need to use your own mind and be aware of what you are doing.
Tor has improve so much in few years in terms of better security and speed(must want to mention that) and continuous development is going on by developers, so I don’t think of any more improvement that tor needs beside been up to date with firefox’s version so that browser patches get implemented quickly in tor browser because browser exploits are the major way to exploit tor network.
Why is the Tor network threatening to law enforcement
Although tor is developed by US navy for privacy and anonymity but currently most user traffic that pass through tor is used for illegal activity like drugs dealing and anti-government activity. Due to tor’s high anonymity nature and these illegal activity tor has became a threat to law enforcement and they start spending large money and resources to take down tor networks.
Illegal activity where provided through tor network hidden services which are really difficult to track down.
But the main goal for tor development is to provide anonymity to a concern user who doesn’t want their identity to get shared to anyone. Tor is also highly important for users who live in places like china and doesn’t have access to certain sites due to internet firewall or other political diplomacy.
It needed to understand that tor in not only for security concerns but for everyone for their internet freedom.
What is ANONABOX (TOR hardware)
Anonabox (link) is an open source embedded networking device(or simply a router) which comes with Tor network pre-installed and configured inside it. Some variants of anonabox also comes with inbuilt vpn services support. The main advantage of using Anonabox is its portable nature, because of which you need not to be worry about installing tor on any new device that you start using or browsing internet on any open network in your near coffee shop.
You can think of anonabox as a normal routing devise that have support of wireless and wired connection and having tor network pre configured inside it, so any traffic pass through that router go through tor network. Ideally anonabox makes use of tor network much easy and robust, hence it comes with many benefits over using tor bundle installed on your system.
Vpn support for extra layer of privacy
Lots of security concern people use vpn with tor network to add a extra layer of anonymity and privacy.
Because of using vpn if somehow your guard node get compromised and your traffic get identified, still the ip address attacker get is the ip from your vpn and not your own public ip. So, now he also need to tackle the vpn provider to get your public ip.
Anonabox come with inbuilt some popular vpn like HMA(Hide my ass) and few more(expect a much larger list in future as mentioned by anonabox team). This will make using the both services easily without any hassel.
You can route entire traffic through tor
If you have installed tor bundle in your machine then by default it comes with tor browser(a firefox browser configured specially to use as a tor client) to surf the web anonymously. Whatever you surf through that browser goes via tor network. But your anonymity can be reveled if you use any other applications that are not configured to use tor network. In that case you need to create SOCKS5 proxy for making the data of that application pass through tor network.
With anonabox, this property is default configure to pass all the data from any application through tor network. Strong profit of using anonabox is that you can somehow fake software but you can’t fake hardware.
Lets take a scenario to understand it better(A real use case reveled from snowden leaks):-
A most popular way of deanonymizing people from tor network as used by spy agencies is through using firefox’s 0days for shell command execution through some piece of javascript code. The assembly code embedded in javascript run as a command in your shell. These commands generally are lightweight like ping to the attacker server. This reveled the original public ip address of the tor user.
But in case with anonabox since all traffic by default pass through tor network, using command like ping doesn’t make any change in your anonymity.
Faster internet while using anonabox?
Some people must want to know that is the browsing speed will increase using anonabox over tor browser alone? Yes, due to own dedicated device for using tor, it doesn't use up system resources on your local computer and hence generally give a faster connectivity. Anonabox come with their own memory and cpu hence seems to be consistently faster than using the TOR browser alone. Altough from inside its just using tor, so most of the speed depend on tor properties only.
Anonabox can be a good solution for non-technical people who is concerned about his privacy while using internet because of its plug and play nature. Its portable and easy to use. But someone who is already using tor may will think twice before purchasing those devices. As people like myself will prefer using tails live bootable dedicated pen drive for same privacy and anonymity. It will cost you less then 10 bucks as compare to a lowest anonabox device which cost you approx 60 dollar. Another caveat with going for the low range anonabox is lacks of power to configure tor. Model like The original doesn’t allow you to change your tor setting, like selecting your own exit node and minimum number of relays etc. People who want full control over their tor network should not prefer purchasing it at first place, rather go will high range device like PRO which cost approx 120 dollars. Other mistake
which I think normal users may do is using their regular browser like google chrome with anonabox device, which can again be a privacy issue because your normal browser are not configured to use for tor and hence can leak some information which can be bad for you anonymity. So, its better to use tor browser with using anonabox devices. Combing both anonabox and tor browser is not only better solution but also a must solution if you don’t want your data to get leaked through some previously saved cookie in your browser or some other way.
Anonabox is a great way to make use of tor much more robust and easy. The devices are selling worldwide and get a good review/support from people. It is a great next step toward internet privacy.